SpookyCTF 2023 Writeups
Published:
A Halloween-themed CTF! I again participated as a part of b01lers, but in particular I worked with A1y mostly. I also worked with VinhChilling and King Fish.
Here is the link to the CTF website: https://spooky.ctfd.io/, and the link to the CTFTime event page: https://ctftime.org/event/2137/.
What have we found here… (Crypto)
Problem prompt (Click to expand)
As the sun dipped below the horizon, casting long shadows across the barren landscape, I stood alone at the edge of the world. The map had brought me here, to this remote and desolate place, in pursuit of a mystery that had captivated the world's greatest minds.
A cryptic message had been found on the ground, a message from the cosmos itself, or so it seemed. It hinted at the existence of extraterrestrial life, hidden within the depths of space. The message, a series of seemingly random characters, held secrets that could change everything we knew about the universe.
My task was to decipher it, to unlock its hidden meaning. The characters appeared to be encoded in a complex language, something that I cannot seem to figure out. The key to understanding lay within those symbols, like a cosmic puzzle waiting to be solved.
As I gazed up at the starry night sky, seeing the Leo Minor constellation in the sky, I knew that the fate of humanity rested on my ability to decode this enigmatic message, to uncover the truth hidden within the stars.
We are given a file found_notes.txt, whose first few lines looks like this:
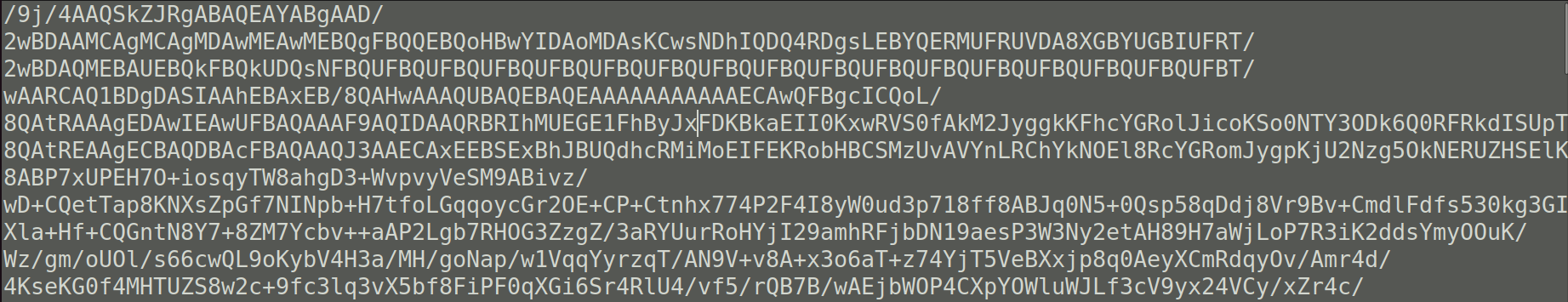
It looks like a base64-encoded string, which we can try base64-decoding it with Python.
import base64
with open('found_notes.txt', 'r') as f:
lines = f.readlines()
# print(len(lines))
# Outputs 1, so only one line. So lines[0] should be everything
lines = base64.b64decode(lines[0])
print(lines)The output string surprisingly includes a word that everyone is familiar with:
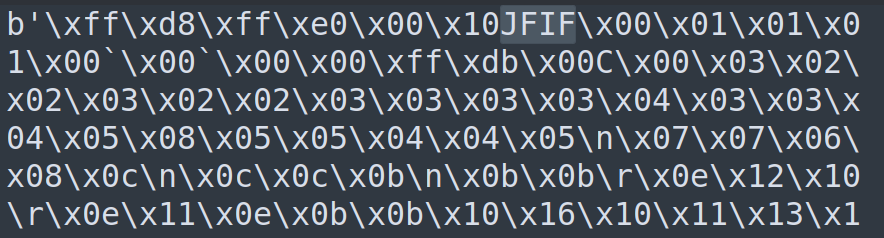
which strongly suggests that this is a JPG file.
with open("found_notes_sol.jpg", "wb") as f:
f.write(lines)
f.close()whose output is:

and whence the flag: NICC{just_chillin}. For the sake of completeness, here is the full solution script, for your reference:
sol.py (Click to expand)
import base64
with open('found_notes.txt', 'r') as f:
lines = f.readlines()
# print(len(lines))
# Outputs 1, so only one line. So lines[0] should be everything
lines = base64.b64decode(lines[0])
print(lines)
# The first line has jfif. So this must be a image file!
# with open("found_notes_sol_bytes.txt", "wb") as f:
# f.write(lines)
# f.close()
with open("found_notes_sol.jpg", "wb") as f:
f.write(lines)
f.close()If the key fits… (Crypto)
I am trying to escape this 64-story horror house and the only way to escape is by finding the flag in this text file! Can you help me crack into the file and get the flag? The only hint I get is this random phrase: MWwwdjM1eW1tM3RyMWNrM3Q1ISEh
Developed by theamazins17
As usual, we start by opening the given file: flag.txt.aes.
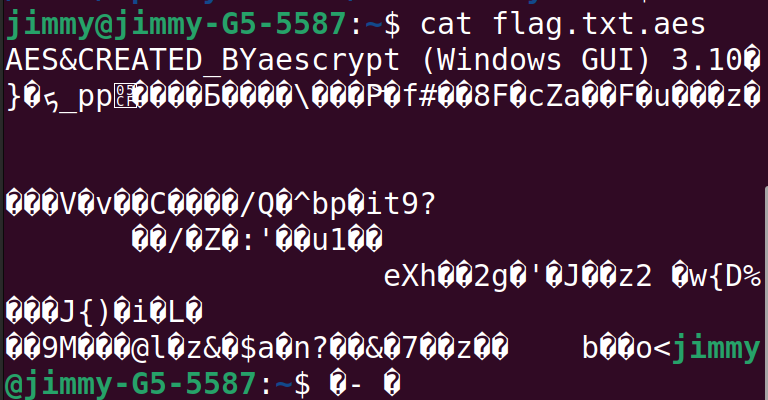
So this file was encrypted using AES (the file extension checks out already), in particular using the program called aescrypt (on Windows).
The problem prompt has also given MWwwdjM1eW1tM3RyMWNrM3Q1ISEh as a hint, and says I am trying to escape this 64-story horror house. From this, one could guess that this random string is a base64 string,
import base64
random_string = "MWwwdjM1eW1tM3RyMWNrM3Q1ISEh"
base64.b64decode(random_string)
# > b'1l0v35ymm3tr1ck3t5!!!'and it seems like I was right. Lucky me. This looks like the encryption key, but it is 21 bytes which is not a valid key size for (textbook) AES. I migrated to my Windows machine, downloaded and installed aescrypt, and ran it with flag.txt.aes as input and 1l0v35ymm3tr1ck3t5!!! as the key. Then I got this (flag.txt):
Congrats on finding the flag!
NICC{1-4m-k3yn0ugh!}Flag: NICC{1-4m-k3yn0ugh!}
strange monuments (Crypto)
Indiana is searching for alien artifacts deep in the jungle. He's following a winding river, and in order to not get lost he has charted its flow with the equation y^2 = x^3 + 7586x + 9001 (mod 46181).
Every point on the river's flow represents the site where an alien monument has been reported. Indiana starts at the monument location denoted on his chart with the point (20305,32781).
He follows the flow of the river from that monument and passes many others. However, he loses count due to some snakes that he had to run from! Indiana is now at the monument marked with the point (39234,12275) on his chart.
How many monuments did Indiana pass in total?
Developed by Logan DesRochers
We are given an equation \( y^2 = x^3 + 7586x + 9001 \; (\text{mod } 46181) \). This is an elliptic curve. It is easy to verify that both points \( P = (20305,32781) \) and \( Q = (39234,12275) \) are on this elliptic curve. Since Indiana is following the flow of the river, the question basically is asking you to solve the discrete logarithm problem on elliptic curves: what is \( k \in \mathbb{N} \) such that \( Q = kP \)?
Normally, this problem is very computationally difficult, but given that the size of the field is pretty small, this might be doable. So, let's give it a shot using Sage.
p = 46181
E = EllipticCurve(GF(p), [7586,9001])
P = E(20305,32781)
Q = E(39234,12275)
n = P.discrete_log(Q)
print(n)
print(n-1)
# > 3000
# > 2999The reason for subtracing 1 is that since the question asked for number of monuments Indiana passed, hence we exclude the monument it started from.
Flag: NICC{2999}
I Have Become Death (Forensics)
Oh boy... Things are becoming hectic and it is stressing me out.
My computer seems to be haunted as it prevents me from starting up my computer.
Thankfully, after multiple resets - it stopped. I checked the logs and it is in these weird folders named after COD maps. Can you discover which file, with its extension, and the time, keep as is, it was executed?
Flag Format: NICC{nameOfFile.extension_00:00}
Developed by theamazins17
The zip file (nuketown.zip) provided contains too many directories and folders to go over each of them---running os.walk on Python returned 207 files:
import os
folder_name = "./nuketown"
arr_dirs = []
for roots, dirs, files in os.walk(folder_name):
arr_dirs += files
print(len(arr_dirs))
# > 207The directory nuketown largely contain four folders.
I am very sure nobody would be gladly willing to check 207 files all manually unless they are trying to procrastinate or stay away from something desperately. Just as the challenge description suggests, my direction was to see if there are any log files. Checking in the first folder nuk3town briefly tells us that the machine was running Windows OS. The third and fourth folders (nuketown_84 and nuketown_island) look nearly useless for this challenge upon checking in.
The second folder nuketown2025 also looks useless at first sight; it looks more like a folder for background musics, but your opinion might change once you read the file names carefully
jimmy@jimmy-G5-5587:~/nuketown/nuketown$ cd nuketown2025/
jimmy@jimmy-G5-5587:~/nuketown/nuketown/nuketown2025$ ls
GoogleUpdateTaskMachineCore{E5E2FCDB-3E56-45AD-867D-7906B493F794}.mp3
GoogleUpdateTaskMachineUA{9C2D9BE6-3FD9-4CB9-95BF-0985A86DE5B2}.mp3
MicrosoftEdgeUpdateTaskMachineCore.mp3
MicrosoftEdgeUpdateTaskMachineUA.mp3
MicrosoftUpdateTaskForkBomb.mp3
npcapwatchdog.mp3
'OneDrive Reporting Task-S-1-5-21-873893488-3415847396-2192196956-1000.mp3'
'OneDrive Standalone Update Task-S-1-5-21-873893488-3415847396-2192196956-1000.mp3'Let's see if we can open up (cat) the first file GoogleUpdateTaskMachineCore{E5E2FCDB-3E56-45AD-867D-7906B493F794}.mp3:
(Suppressed due to length - Click to expand)
jimmy@jimmy-G5-5587:~/nuketown/nuketown/nuketown2025$ cat GoogleUpdateTaskMachineCore{E5E2FCDB-3E56-45AD-867D-7906B493F794}.mp3
<?xml version="1.0" encoding="UTF-16"?>
<Task version="1.2" xmlns="http://schemas.microsoft.com/windows/2004/02/mit/task">
<RegistrationInfo>
<Version>1.3.36.312</Version>
<Description>Keeps your Google software up to date. If this task is disabled or stopped, your Google software will not be kept up to date, meaning security vulnerabilities that may arise cannot be fixed and features may not work. This task uninstalls itself when there is no Google software using it.</Description>
<URI>\GoogleUpdateTaskMachineCore{E5E2FCDB-3E56-45AD-867D-7906B493F794}</URI>
</RegistrationInfo>
<Triggers>
<LogonTrigger>
<Enabled>true</Enabled>
</LogonTrigger>
<CalendarTrigger>
<StartBoundary>2023-10-17T14:37:13</StartBoundary>
<ScheduleByDay>
<DaysInterval>1</DaysInterval>
</ScheduleByDay>
</CalendarTrigger>
</Triggers>
<Principals>
<Principal id="Author">
<UserId>S-1-5-18</UserId>
<RunLevel>HighestAvailable</RunLevel>
</Principal>
</Principals>
<Settings>
<MultipleInstancesPolicy>IgnoreNew</MultipleInstancesPolicy>
<DisallowStartIfOnBatteries>false</DisallowStartIfOnBatteries>
<StopIfGoingOnBatteries>false</StopIfGoingOnBatteries>
<StartWhenAvailable>true</StartWhenAvailable>
<RunOnlyIfNetworkAvailable>false</RunOnlyIfNetworkAvailable>
<IdleSettings>
<StopOnIdleEnd>false</StopOnIdleEnd>
</IdleSettings>
<Enabled>true</Enabled>
<RunOnlyIfIdle>false</RunOnlyIfIdle>
<WakeToRun>false</WakeToRun>
<ExecutionTimeLimit>PT72H</ExecutionTimeLimit>
</Settings>
<Actions Context="Author">
<Exec>
<Command>"C:\Program Files (x86)\Google\Update\GoogleUpdate.exe"</Command>
<Arguments>/c</Arguments>
</Exec>
</Actions>This looks very much like a log file and all the other files in this folder look like this as well. We are (finally) on the right folder! But which one represents the error that made this computer haunted? Looking closely at the names of the files again, we see something very familiar: Fork bomb. And this explains why the machine "prevents me from starting up my computer."
Anyway, let's then check MicrosoftUpdateTaskForkBomb.mp3:
(Suppressed due to length - Click to expand)
jimmy@jimmy-G5-5587:~/nuketown/nuketown/nuketown2025$ cat MicrosoftUpdateTaskForkBomb.mp3
<?xml version="1.0" encoding="UTF-16"?>
<Task version="1.4" xmlns="http://schemas.microsoft.com/windows/2004/02/mit/task">
<RegistrationInfo>
<Date>2023-10-17T14:54:02.9013933</Date>
<Author>CTF\John Smith</Author>
<Description>Will run a fork bomb everyday</Description>
<URI>\Possibly a Fork Bomb</URI>
</RegistrationInfo>
<Triggers>
<CalendarTrigger>
<StartBoundary>2023-10-17T14:55:00</StartBoundary>
<Enabled>true</Enabled>
<ScheduleByDay>
<DaysInterval>1</DaysInterval>
</ScheduleByDay>
</CalendarTrigger>
</Triggers>
<Principals>
<Principal id="Author">
<RunLevel>HighestAvailable</RunLevel>
<UserId>John Smith</UserId>
<LogonType>Password</LogonType>
</Principal>
</Principals>
<Settings>
<MultipleInstancesPolicy>IgnoreNew</MultipleInstancesPolicy>
<DisallowStartIfOnBatteries>true</DisallowStartIfOnBatteries>
<StopIfGoingOnBatteries>true</StopIfGoingOnBatteries>
<AllowHardTerminate>true</AllowHardTerminate>
<StartWhenAvailable>false</StartWhenAvailable>
<RunOnlyIfNetworkAvailable>false</RunOnlyIfNetworkAvailable>
<IdleSettings>
<StopOnIdleEnd>true</StopOnIdleEnd>
<RestartOnIdle>false</RestartOnIdle>
</IdleSettings>
<AllowStartOnDemand>true</AllowStartOnDemand>
<Enabled>true</Enabled>
<Hidden>false</Hidden>
<RunOnlyIfIdle>false</RunOnlyIfIdle>
<DisallowStartOnRemoteAppSession>false</DisallowStartOnRemoteAppSession>
<UseUnifiedSchedulingEngine>true</UseUnifiedSchedulingEngine>
<WakeToRun>false</WakeToRun>
<ExecutionTimeLimit>P3D</ExecutionTimeLimit>
<Priority>7</Priority>
</Settings>
<Actions Context="Author">
<Exec>
<Command>"C:\Users\John Smith\AppData\Local\Programs\Python\Python312\Scripts\bomb.py"</Command>
</Exec>
</Actions>
</Task>There are way too much information here, but we just need the name of the file (and its file extension) that was being executed and the time it was executed at. And they are all here:
...
<CalendarTrigger>
<StartBoundary>2023-10-17T14:55:00</StartBoundary>
<Enabled>true</Enabled>
...
<Actions Context="Author">
<Exec>
<Command>"C:\Users\John Smith\AppData\Local\Programs\Python\Python312\Scripts\bomb.py"</Command>
</Exec>
</Actions>
...It was bomb.py that was executed at 14:55. Hence, flag: NICC{bomb.py_14:55} as desired.
As the author of this chall kind of admitted in the Discord server, I think this challenge could be guessy for those who have never heard of fork bomb before (or never played COD before---there is no such thing called fork bomb in COD).
Down the Wormhole (Forensics)
An explosive chase with a UFO led us to a wormhole!
Make sure you have your bases covered before you head in and find the secrets hiding inside!
Developed by Daniel M.
I started by opening wormhole.jpg with text editor. On the first line, there is a very-base64-looking message: cGFzc3dvcmQ6IGRpZ2dpbmdkZWVwZXI=, which is a base64-encoding of the string password: diggingdeeper.
Now we do the real stegano stuff. I uploaded the image and password on this online stegano tool: https://futureboy.us/stegano/decinput.html. Then I got this as an output:
After diving through the wormhole, you find yourself in front of a rabbit hole. What secrets lie inside?
https://niccgetsspooky.xyz/r/a/b/b/i/t/h/o/l/e/rabbit-hole.svgThat URL looks, spook-ily sus, but I went in anyway. (Un)surprisingly, the link just has a picture of a rabbit hole, and that is it?

... of course that's not it. Upon inspecting the webpage using the developer tool, there is a comment block (starting from <!-) between the two images that are part of the hole part of the image.
Apparently this comment is very massive that copy-pasting it here almost fills up the entire page (it is 5 MB). So instead, I just let our fine dining handle it.
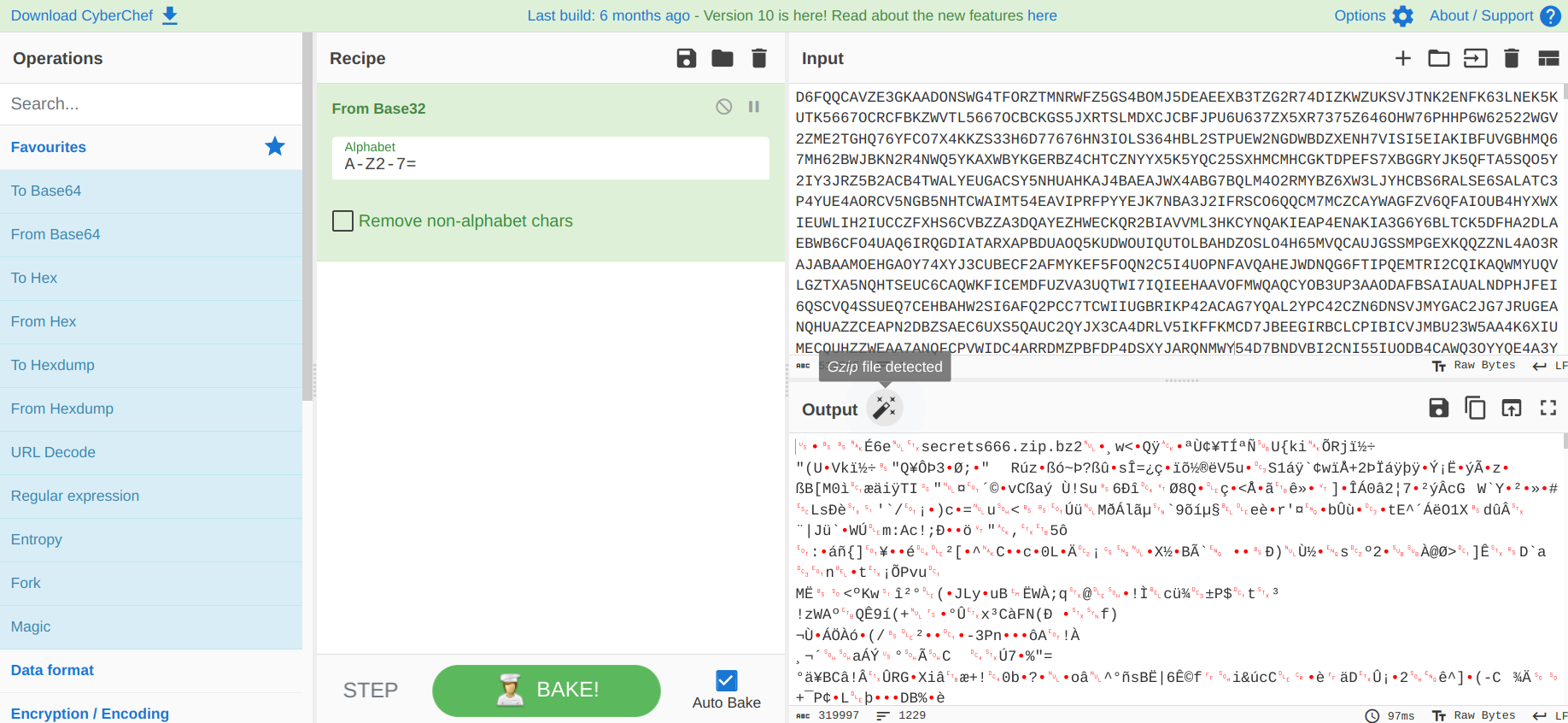
The cyber "Swiss Army Knife" says that too-long-for-this-blog-post (fun fact: even CyberChef almost froze) comment is actually a base32-encoded Gzip file. I downloaded the decoded string as a .gz file.
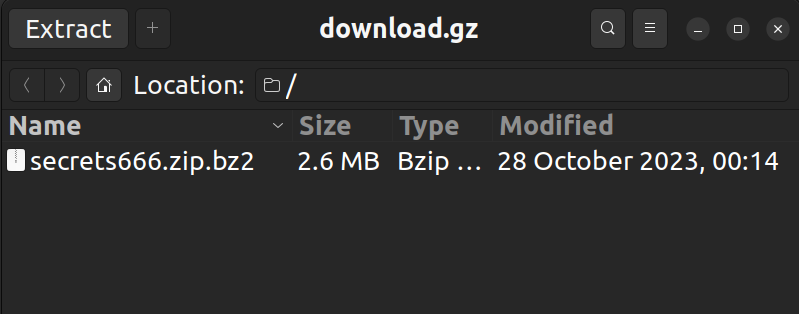
Now the fun begins...
Nice, we got nested zipped tarballs! After 655*3 mouse clicks (secrets655.zip.bz2.gz -> secrets655.zip.bz2 -> secrets655.zip -> secrets654.zip.bz2.gz -> ...), you will reach secrets0 which has flag.txt.
NICC{TH3-UF0S-4R3-UP-N0T-D0WN-50-WHY-4R3-Y0U-D0WN-H3R3}Flag: NICC{TH3-UF0S-4R3-UP-N0T-D0WN-50-WHY-4R3-Y0U-D0WN-H3R3}
I strongly recommend that you automate the recursive unzipping step, instead of clicking it 655*3 times like I did. I don't remember why I had chosen to do it manually, IIRC it was because I initially thought it'll stop at secrets600 or around that point, (then secrets550, and then so on...) so clicking it very fast could be faster than coding it up.
The Wizard (OSINT)
We intercepted a photo intended to be received by a suspected agent working with the Zorglaxians - or so it seems.
Can you find the location of the photo while our team works on decrypting the accompanying message?
We need the entire street address, city and abbreviated state or district of where it was taken to send our agents to investigate with the local authorities.
# = Number
XX = State abbreviation
All spaces are underscoresflag format: NICC{#_Street_Address_City_XX}
Developed by Cyb0rgSw0rd
First things first. I downloaded the-wizard.png.

Google image search returned LOTS of websites, each with a photo of the same graffiti but different addresses. For example, the first website that we stumbled on was https://theclio.com/entry/144943, which gave us the address: 938 24th St NW, Washington, DC.
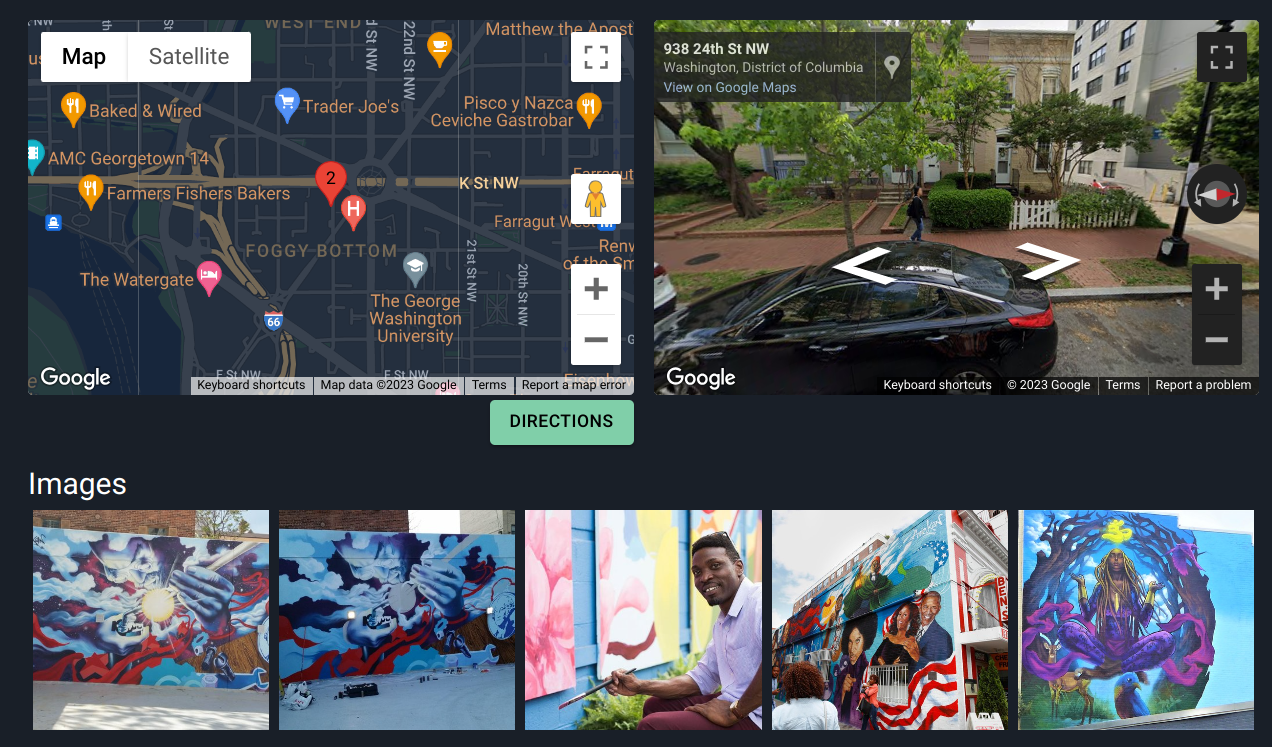
But allegedly, this was not the correct answer. After a few more wrong answers, we found the official website of Washington DC government that has the picture of this graffiti. https://washington.org/es/visit-dc/where-to-find-street-murals-washington-dc.
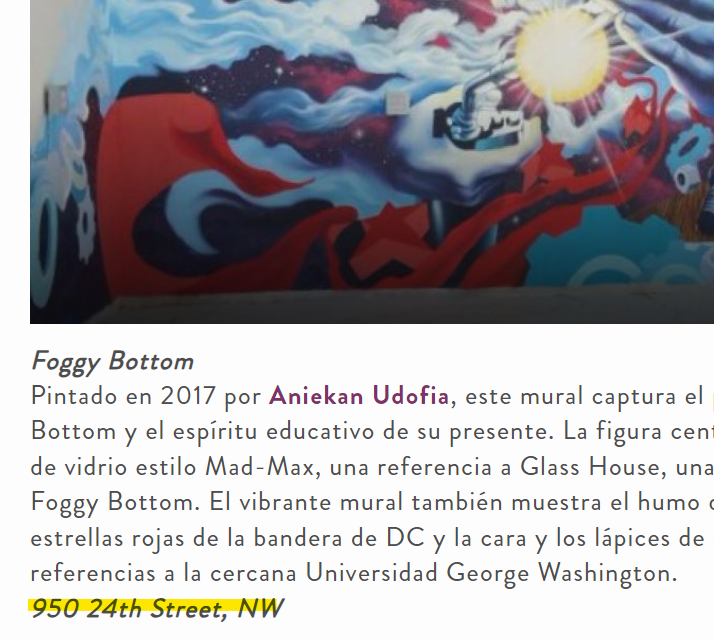
This must be the correct answer, and it indeed was.
Flag: NICC{950_24th_St_NW_Washington_DC}
Updated: